DOI: 10.37421/1736-4337.2022.16.362
DOI: 10.37421/1736-4337.2022.16.366
Since it was first proposed in 2018, researchers have paid attention to the concept of verifiable delay functions. Verifiable delay has numerous applications in blockchain research, including: computational timestamping, public random beacons, blockchains that use fewer resources and data replication proofs This paper provides an overview of the various types of verifiable delay functions as well as an introduction to the concept of verifiable delay functions. First, weak verifiable delay functions, incremental verifiable delay functions, decodable verifiable delay functions and trapdoor verifiable delay functions are introduced, along with their descriptions and characteristics. Two security assumptions are typically used to construct verifiable delay functions: structural assumption or algebraic assumption. On the basis of cryptography theory, the security assumptions of two distinct verifiable delay functions are then described. Second, a super-singular isogeny-based post-quantum verifiable delay function is presented. The paper concludes by providing a synopsis of the blockchain-related uses of verifiable delay functions.
DOI: 10.37421/1736-4337.2022.16.363
DOI: 10.37421/1736-4337.2022.16.364
DOI: 10.37421/1736-4337.2022.16.365
This study addresses the numerical solution of a nonlocal boundary-value issue for a two-dimensional pseudoparabolic equation that arises in a variety of physical events. For the solution of this problem, a three-layer alternating direction implicit approach is examined. Peaceman-ADI Rachford's approach for the 2D parabolic equation is generalised in this method. The suggested method's stability is demonstrated in the specific norm. To demonstrate its stability, we study the algebraic eigenvalue problem using nonsymmetric matrices.
DOI: 10.37421/1736-4337.2025.19.495
DOI: 10.37421/1736-4337.2025.19.496
DOI: 10.37421/1736-4337.2025.19.497
DOI: 10.37421/1736-4337.2025.19.498
DOI: 10.37421/1736-4337.2025.19.499
DOI: 10.37421/1736-4337.2025.19.500
DOI: 10.37421/1736-4337.2025.19.501
DOI: 10.37421/1736-4337.2025.19.502
DOI: 10.37421/1736-4337.2025.19.503
DOI: 10.37421/1736-4337.2025.19.504
DOI: 10.37421/1736-4337.2025.19.485
DOI: 10.37421/1736-4337.2025.19.486
DOI: 10.37421/1736-4337.2025.19.487
DOI: 10.37421/1736-4337.2025.19.488
DOI: 10.37421/1736-4337.2025.19.489
DOI: 10.37421/1736-4337.2025.19.490
DOI: 10.37421/1736-4337.2025.19.491
DOI: 10.37421/1736-4337.2025.19.492
DOI: 10.37421/1736-4337.2025.19.493
DOI: 10.37421/1736-4337.2025.19.494
DOI: 10.37421/1736-4337.2024.18.475
DOI: 10.37421/1736-4337.2024.18.476
DOI: 10.37421/1736-4337.2024.18.478
DOI: 10.37421/1736-4337.2024.18.479
DOI: 10.37421/1736-4337.2024.18.480
DOI: 10.37421/1736-4337.2024.18.481
DOI: 10.37421/1736-4337.2024.18.482
DOI: 10.37421/1736-4337.2024.18.483
DOI: 10.37421/1736-4337.2024.18.484
DOI: 10.37421/1736-4337.2024.18.477
DOI: 10.37421/1736-4337.2024.18.464
DOI: 10.37421/1736-4337.2024.18.465
DOI: 10.37421/1736-4337.2024.18.466
DOI: 10.37421/1736-4337.2024.18.467
DOI: 10.37421/1736-4337.2024.18.468
DOI: 10.37421/1736-4337.2024.18.469
DOI: 10.37421/1736-4337.2024.18.470
DOI: 10.37421/1736-4337.2024.18.471
DOI: 10.37421/1736-4337.2024.18.472
DOI: 10.37421/1736-4337.2024.18.473
M. L. Ahmed Oubeid*, A. Benkirane and M. Sidi El Vally
DOI: 10.37421/1736-4337.2024.18.426
We prove the existence of solutions of nonlinear parabolic problems with measure data in Musielak-Orlicz-Sobolev spaces.
DOI: 10.37421/1736-4337.2024.18.427
Based upon the data and assessment hypothesis, this paper proposes a "differential common data" (DMI) rule to defend the security insurance (PP). Algorithmically, DMI-ideal arrangements can be inferred by means of the Discriminant Part Investigation (DCA). In addition, DCA has two machine learning variants that are suitable for supervised learning applications—one in the kernel space and the other in the original space. CP unifies the conventional Information Bottleneck (IB) and Privacy Funnel (PF) and results in two constrained optimizers known as Generalized Information Bottleneck (GIB) and Generalized Privacy Funnel (GPF) by extending the concept of DMI to the utility gain and privacy loss. DCA can be further extended to a DUCA machine learning variant in supervised learning environments to achieve the best possible compromise between utility gain and privacy loss. Finally, a golden-section iterative method is developed specifically for the two constrained optimization problems in order to speed up convergence: GPF and GIB. Data bottleneck and security channel issues are critical challenges in data transmission and communication. Data bottleneck arises when the rate of data production or transfer exceeds the capacity of the communication channel or system. Security channel issues involve vulnerabilities that compromise the confidentiality, integrity, or availability of transmitted data. This article provides an overview of these challenges, their causes and implications. It discusses strategies for addressing data bottleneck, such as optimizing bandwidth, storage and processing capabilities. It also explores security measures, including authentication, encryption and intrusion detection, to mitigate security channel issues. A holistic approach integrating efficient data management and robust security practices is crucial for ensuring smooth and secure information flow. This paper investigates a Compressive Security (CP) philosophy for ideal tradeoff between utility increase and protection misfortune. CP addresses an aspect diminished subspace plan of ideally desensitized question that might be securely imparted to the general population.
DOI: 10.37421/1736-4337.2024.18.428
DOI: 10.37421/1736-4337.2024.18.429
DOI: 10.37421/1736-4337.2024.18.430
Algorithmically, DMI-ideal arrangements can be inferred by means of the Discriminant Part Investigation (DCA). In addition, DCA has two machine learning variants that are suitable for supervised learning applications—one in the kernel space and the other in the original space. CP unifies the conventional Information Bottleneck (IB) and Privacy Funnel (PF) and results in two constrained optimizers known as Generalized Information Bottleneck (GIB) and Generalized Privacy Funnel (GPF) by extending the concept of DMI to the utility gain and privacy loss. DCA can be further extended to a DUCA machine learning variant in supervised learning environments to achieve the best possible compromise between utility gain and privacy loss. Finally, a golden-section iterative method is developed specifically for the two constrained optimization problems in order to speed up convergence: GPF and GIB. Data bottleneck and security channel issues are critical challenges in data transmission and communication. Data bottleneck arises when the rate of data production or transfer exceeds the capacity of the communication channel or system. Security channel issues involve vulnerabilities that compromise the confidentiality, integrity, or availability of transmitted data. This article provides an overview of these challenges, their causes and implications. It discusses strategies for addressing data bottleneck, such as optimizing bandwidth, storage and processing capabilities. It also explores security measures, including authentication, encryption and intrusion detection, to mitigate security channel issues. A holistic approach integrating efficient data management and robust security practices is crucial for ensuring smooth and secure information flow. This paper investigates a Compressive Security (CP) philosophy for ideal tradeoff between utility increase and protection misfortune. CP addresses an aspect diminished subspace plan of ideally desensitized question that might be securely imparted to the general population. Based upon the data and assessment hypothesis, this paper proposes a "differential common data" (DMI) rule to defend the security insurance (PP).
DOI: 10.37421/1736-4337.2024.18.431
DOI: 10.37421/1736-4337.2024.18.435
Geometry and algebra have long been considered distinct branches of mathematics, each with its own set of principles, methods, and applications. However, the intersection of these two fields has led to a deeper understanding of mathematical structures and their relationships. In this article, we explore the concept of a unified approach to geometry and algebraic structures, showcasing how insights from both disciplines can enrich our understanding and provide powerful tools for solving problems across various domains.
DOI: 10.37421/1736-4337.2024.18.434
DOI: 10.37421/1736-4337.2024.18.433
Madan Mohan Shastri* and Anu Dey
DOI: 10.37421/1736-4337.2024.18.432
Algebraic structures form the backbone of modern mathematics, providing a framework for understanding and analyzing mathematical objects and their relationships. From the foundational concepts of groups and rings to the more advanced structures like Lie superalgebras, algebraic structures play a crucial role in various branches of mathematics, physics, and beyond. This article takes a comprehensive journey through the landscape of algebraic structures, exploring their definitions, properties, and applications.
DOI: 10.37421/1736-4337.2023.17.391
DOI: 10.37421/1736-4337.2023.17.391
DOI: 10.37421/1736-4337.2023.17.386
This paper investigates a Compressive Security (CP) philosophy for ideal tradeoff between utility increase and protection misfortune. CP addresses an aspect diminished subspace plan of ideally desensitized question that might be securely imparted to the general population. Based upon the data and assessment hypothesis, this paper proposes a "differential common data" (DMI) rule to defend the security insurance (PP). Algorithmically, DMI-ideal arrangements can be inferred by means of the Discriminant Part Investigation (DCA). In addition, DCA has two machine learning variants that are suitable for supervised learning applications—one in the kernel space and the other in the original space. CP unifies the conventional Information Bottleneck (IB) and Privacy Funnel (PF) and results in two constrained optimizers known as Generalized Information Bottleneck (GIB) and Generalized Privacy Funnel (GPF) by extending the concept of DMI to the utility gain and privacy loss. DCA can be further extended to a DUCA machine learning variant in supervised learning environments to achieve the best possible compromise between utility gain and privacy loss. Finally, a golden-section iterative method is developed specifically for the two constrained optimization problems in order to speed up convergence: GPF and GIB. Data bottleneck and security channel issues are critical challenges in data transmission and communication. Data bottleneck arises when the rate of data production or transfer exceeds the capacity of the communication channel or system. Security channel issues involve vulnerabilities that compromise the confidentiality, integrity, or availability of transmitted data. This article provides an overview of these challenges, their causes and implications. It discusses strategies for addressing data bottleneck, such as optimizing bandwidth, storage and processing capabilities. It also explores security measures, including authentication, encryption and intrusion detection, to mitigate security channel issues. A holistic approach integrating efficient data management and robust security practices is crucial for ensuring smooth and secure information flow.
DOI: 10.37421/1736-4337.2023.17.394
DOI: 10.37421/1736-4337.2023.17.392
DOI: 10.37421/1736-4337.2023.17.393
The general case of a material belonging to an unknown class of constitutive behavior is the focus of our recently developed EUCLID method for unsupervised automated discovery of material laws. To this end, we influence the hypothesis of summed up standard materials, which envelops a plenty of significant constitutive classes including flexibility, thickness, versatility and erratic blends thereof. That's what we show, dependent just upon full-field kinematic estimations and net response powers, EUCLID can naturally find the two scalar thermodynamic possibilities, to be specific, the Helmholtz free energy and the dissemination potential, which totally characterize the way of behaving of summed up standard materials.
DOI: 10.37421/1736-4337.2023.17.387
We argue in this paper that deep properties of discourse structure can be revealed by mapping discourse representations to networks and analyzing them using tools from network theory. Two talk clarified corpora, C58 and STAC, that have a place with various talk types and dialects were looked at and examined. The discourse representations of both corpora were based on a variety of key network indices, which demonstrate the distinct network profiles of the two kinds of discourse. In addition, strong tendencies in building or avoiding the construction of discourse relations between utterances for permissible three-node discourse subgraphs were illuminated by the discovery of both network motifs and antimotifs for the discourse networks in the two corpora. New discourse structure rules based on the properties of the networks that underpin discourse representation may emerge as a result of these findings.
DOI: 10.37421/1736-4337.2023.17.390
DOI: 10.37421/1736-4337.2023.17.389
DOI: 10.37421/1736-4337.2023.17.388
DOI: 10.37421/1736-4337.2023.17.383
DOI: 10.37421/1736-4337.2023.17.381
In mathematics, specifically in algebraic geometry, an irreducible component refers to a subset of a space that is not the union of two proper subsets, each of which is itself closed. In other words, an irreducible component is a maximal subset that cannot be decomposed into smaller closed subsets. In this article, we will explore the concept of irreducible components in depth and provide some examples to help illustrate the concept.
DOI: 10.37421/1736-4337.2023.17.382
Lie theory, also known as the theory of Lie groups, is a branch of mathematics that studies continuous symmetry, especially in the context of smooth manifolds. Lie theory provides a mathematical framework to describe the symmetries of physical systems, from the motion of planets to the behavior of subatomic particles. The theory also plays a crucial role in many areas of modern mathematics, including differential geometry, representation theory, algebraic geometry and mathematical physics. This article provides an introduction to Lie theory, starting with the basics of Lie groups and Lie algebras and progressing to more advanced topics such as Lie's third theorem and the classification of semisimple Lie algebras.
DOI: 10.37421/1736-4337.2023.17.384
DOI: 10.37421/1736-4337.2023.17.385
DOI: 10.37421/1736-4337.2022.16.358
Symmetric spaces are a class of mathematical objects that have played a crucial role in many areas of mathematics, including differential geometry, topology, Lie theory and representation theory. These spaces are characterized by their symmetry groups, which are groups of transformations that preserve some intrinsic structure on the space. In this article, we will discuss the basic properties of symmetric spaces and their applications in various areas of mathematics.
DOI: 10.37421/1736-4337.2022.16.360
DOI: 10.37421/1736-4337.2022.16.361
DOI: 10.37421/1736-4337.2022.16.359
DOI: 10.37421/1736-4337.2022.16.357
A topology is the layout or configuration of a computer network. It defines how computers and other devices are connected to each other and how data is transmitted between them. There are several types of topologies, each with its own advantages and disadvantages. In this article, we will discuss the bus topology consists of a single cable that connects all the devices in a network. Each device is connected to the cable using a T-connector. Data is transmitted along the cable in both directions and each device on the network can access it. The advantage of a bus topology is that it is simple and easy to install. However, if the cable is damaged, the entire network will be affected. Additionally, as more devices are added to the network, the speed of data transmission may decrease. A star topology consists of a central hub or switch that is connected to each device in the network. Each device is connected to the hub using a separate cable.
Emilia Clark
Combinatorial pure mathematics may be a mixing of principles from the areas of Combinatorics and pure mathematics. It deals with combos and arrangements of geometric objects and with separate properties of those objects. It's involved with such topics as packing, covering, coloring, folding, symmetry, tiling, partitioning, decomposition, and illumination issues. Combinatorial pure mathematics includes aspects of topology, graph theory, range theory, and different disciplines.
Joshua Jerry
The Riemann hypothesis is a fundamental mathematical conjecture that has huge implications for the rest of math. It forms the foundation for many other mathematical ideas — but no one knows if it's true. Its validity has become one of the most famous open questions in mathematics.
Rupali Saxena
A number framework is characterized as an arrangement of writing to communicate numbers. It is the numerical documentation for addressing quantities of a given set by utilizing digits or different images in a predictable way. It gives a one-of-a-kind portrayal of each number and addresses the number-crunching and logarithmic design of the figures. It additionally permits us to work on math tasks like option, deduction, and division.
Olivia John
On behalf of the editors of the Journal of Generalized Lie Theory and Applications, I would like to express my sincere gratitude to the reviewers for assessing manuscripts. The editors greatly appreciate the contribution of reviewers who have dedicated their valuable time and efforts in reviewing the assigned manuscripts, which is crucial to the journal’s editorial decision-making process. The Journal of Generalized Lie Theory and Applications follows a double-blind peer-review process, where the identities of both the authors and reviews are not disclosed, to avoid any biases. Committing to review is a diligent task, requiring not only careful reading, analysis, and commentary but also a willingness to continue with a manuscript through multiple revisions. The Journal has taken several steps to thank and acknowledge the reviewers. All articles that are published with the Journal are included in the indexing and abstracting coverage of Index Copernicus, Google Scholar, Open J Gate, Genamics JournalSeek, zbMATH, RefSeek, Project Euclid, MIAR, and EBSCO A-Z.
Alice Johnson
Journal of Generalized Lie Theory and Applications is one of the preferred journals in the field of Applied Mathematics. Journal of Generalized Lie Theory and Applications is a high-quality peer-reviewed journal, containing several high-quality and unique articles, accepting manuscripts for Volume 15 Issue 1. This journal covers the wide-area that involves the following topics, but is not limited to; Lie Algebra, Superalgebra, Combinatorics, Geometry, Combinatorial Geometry, Lie theory, Number System, Homological Algebra, Representation theory, Differential Topology.
DOI: 10.37421/1736-4337.2022.16.353
DOI: 10.37421/1736-4337.2022.16.355
Analyses of brain activity revealed that arithmetic activated more of the bilateral supplementary motor area, left insula and left inferior parietal lobule, while algebra activated more of the angular gyrus. For algebra, significant brain-behavior correlations were found in the semantic network, including the middle temporal gyri, inferior frontal gyri, dorsomedial prefrontal cortices and left angular gyrus. Interindividual single-trial brainbehavior correlation The phonological network, which included the precentral gyrus and supplementary motor area and the visuospatial network, which included the bilateral superior parietal lobules, contained the significant brain-behavior correlations for arithmetic. The visuospatial and semantic networks were found to have significant positive functional connectivity in algebra, while only the visuospatial and phonological networks were found to have significant positive functional connectivity in arithmetic.
DOI: 10.37421/1736-4337.2022.16.354
A time-tree is a rooted phylogenetic tree with all internal and leaf nodes equipped with absolute divergence and sampling dates, respectively. Although these time-trees have emerged as a major focus of phylogenetics research, little is known about their parameter space. From a graphtheoretic and algorithmic point of view, we present and investigate a hierarchy of discrete time-tree space approximations in this article. The NNI graph, one of the most fundamental and widely used phylogenetic graphs, is our hierarchy's lowest level and roughest approximation. The sampling dates and relative timing of evolutionary divergence are discretized by more refined approximations.
DOI: 10.37421/1736-4337.2022.16.356
DOI: 10.37421/1736-4337.2022.16.348
The study offers the entire classification of automorphic Lie algebras based on sln(C), where sln(C) contains no trivial summands, the poles are in any of the exceptional G-orbits in C and the symmetry group G acts on sln(C) through inner automorphisms. The analysis of the algebras within the framework of traditional invariant theory is a crucial aspect of the categorization. This offers both a strong computational tool and raises new concerns from an algebraic standpoint (such as structure theory) that indicate to other uses for these algebras outside of the realm of integrable systems. The study demonstrates, in particular, that the class of automorphic Lie algebras connected to TOY groups (tetrahedral, octahedral and icosahedral groups) depend solely on the automorphic functions of the group, making them group independent Lie algebras. This may be proven by generalising the classical idea to the case of Lie algebras over a polynomial ring and creating a Chevalley normal form for these algebras.
DOI: 10.37421/1736-4337.2022.16.349
Numerous variations of physical issues, such as those in fluid dynamics, solid mechanics, plasma physics, quantum field theory, as well as in mathematics and engineering, include nonlinear partial differential equations. Systems of nonlinear partial differential equations have also been shown to appear in chemical and biological applications. The analytical analysis of a fully generalised (3+1)-dimensional nonlinear potential Yu- Toda-Sasa-Fukuyama equation, with applications in physics and engineering, is presented in this article. In contrast to earlier study on the problem that has already been done, the extended form of the potential Yu-Toda-Sasa-Fukuyama equation is investigated in greater detail in this paper, leading to the achievement of many novel solutions that are of interest. The nonlinear partial differential equation is fundamentally reduced to an integrable form by the use of the Lie group theory, allowing for direct integration of the outcome.
DOI: 10.37421/1736-4337.2022.16.350
DOI: 10.37421/1736-4337.2022.16.351
Nouf Almutiben*, Edward L. Boone, Ryad Ghanam and G. Thompson
DOI: 10.37421/1736-4337.2022.16.347
In this paper we study the Lie symmetries of the canonical connection on Lie groups for the special case when the Lie algebra has a codimension
two abelian nilradical. In this particular case, we have only one algebra in dimension four, namely A4,12 and three algebras in dimension five; namely 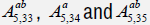 . For each of these algebras we investigate and classify the symmetry algebra associated with its geodesic equations.
. For each of these algebras we investigate and classify the symmetry algebra associated with its geodesic equations.
DOI: 10.37421/1736-4337.2022.16.337
DOI: 10.37421/1736-4337.2022.16.338
DOI: 10.37421/1736-4337.2022.16.339
DOI: 10.37421/1736-4337.2022.16.340
DOI: 10.37421/1736-4337.2022.16.341
DOI: 10.37421/1736-4337.2022.16.334
DOI: 10.37421/1736-4337.2022.16.335
DOI: 10.37421/1736-4337.2022.16.336
DOI: 10.37421/1736-4337.2022.16.333
DOI: 10.37421/1736-4337.2022.16.327
DOI: 10.37421/1736-4337.2022.16.328
DOI: 10.37421/1736-4337.2022.16.329
DOI: 10.37421/1736-4337.2022.16.330
DOI: 10.37421/1736-4337.2022.16.331
DOI: 10.37421/1736-4337.2022.16.321
DOI: 10.37421/1736-4337.2022.16.325
DOI: 10.37421/1736-4337.2022.16.324
DOI: 10.37421/1736-4337.2022.16.323
DOI: 10.37421/1736-4337.2022.16.322
DOI: 10.37421/1736-4337.2022.16.316
DOI: 10.37421/1736-4337.2022.16.317
DOI: 10.37421/1736-4337.2022.16.320
DOI: 10.37421/1736-4337.2022.16.319
DOI: 10.37421/1736-4337.2022.16.318
Manelo Anona
The Lie algebra of isometries of dimension superior than or equal to three is semi-simple if and only if the horizontal nullity space of the Nijenhuis tensor of the canonical connection is reduced to zero and the derivative ideal coincides with algebra.
Olivia Gray
Jessica Brown
Alice Johnson
Alice Johnson